Note: Message from IT Director Ken Sallot on how to minimize “Zoom Bombing.”
Zoom Bombing is where uninvited people join Zoom meetings to be disruptive and create havoc for the attendees of the meeting and can quickly turn a meeting into chaos.
On Tuesday afternoon, UF HR sent out a communication that included a link that included information on securing Zoom meetings to mitigate these types of disruptions. The link is here: https://elearning.ufl.edu/keep-zoom-secure/faculty/.
I have tested some of the mitigation techniques and want to share my thoughts on them.
-
- Setting a Meeting Password – This is probably the easiest to implement and manage, but it runs the risk of having the meeting password posted to social media, which then opens your Zoom meeting up to the outside world. However, in my opinion, this is probably the preferred solution as long as you remind your students not to share the password.To set a meeting password, click the button that says “Require meeting password” when you are creating your meeting.
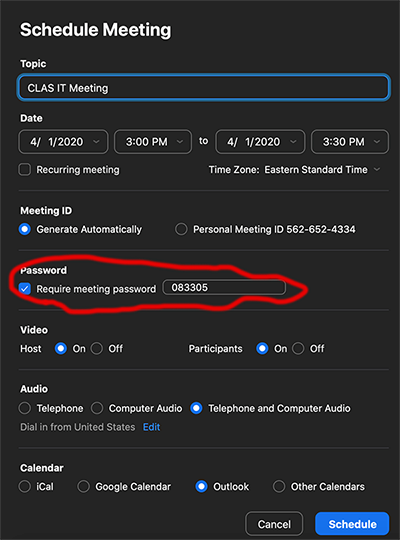
- Please be sure that your participants are aware of the meeting password, otherwise they will not be able to join the meeting.
- Waiting Rooms – A waiting room allows the meeting organizer to control when a person is added to a meeting. When someone tries to connect to a meeting that has a Waiting Room enabled, they are unable to join the meeting until the organizer allows them in.This is an important point, a Waiting Room requires the meeting organizer to be diligent and manually allow individuals to enter the meeting as they attempt to join. I tested Waiting Rooms while hosting a zoom meeting with twenty participants and I found it distracting to manually re-admit a participant that kept disconnecting and reconnecting.In my opinion a Waiting Room is only useful for Zoom calls with a very small number of participants, or perhaps for conducting virtual office hours. I would not consider using Waiting Rooms with more than fifteen participants.
- Allow Only Authenticated Users – This setting is supposed to require everyone to have a Zoom account and to be logged in when using the Zoom app. Unfortunately, after some testing, we verified that this setting currently leaves Zoom meetings open to phone in callers.
- Setting a Meeting Password – This is probably the easiest to implement and manage, but it runs the risk of having the meeting password posted to social media, which then opens your Zoom meeting up to the outside world. However, in my opinion, this is probably the preferred solution as long as you remind your students not to share the password.To set a meeting password, click the button that says “Require meeting password” when you are creating your meeting.
Of the three techniques that are available to restrict Zoom meetings, my opinion is that requiring a password is the most efficient, effective, and secure.
The e-learning site also includes plenty of other useful tips, such as how to remove a participant from a meeting, manage who can share their screen with the group, and more. I encourage everyone to spend a few moments and review the information at https://elearning.ufl.edu/keep-zoom-secure/faculty/.
My best,
Ken Sallot
CLAS IT Director